Cybersecurity Report
Message from Security Officer

The business environment surrounding Concordia Financial Group, Ltd. (the “Company”) is drastically changing at an unprecedented pace, as exemplified by the advancement of declining birthrate and aging population and digitalization as well as heightened awareness of social and environmental issues. Given such environmental changes, we have set our long-term goal as “a solutions company that is rooted in the community and is chosen as a company that works together with the community,” and positioned FY2022 to FY2024 covered by the Medium-Term Management Plan as the “three years to accelerate transformation and materialize results,” with three basic themes of “Growth,” “Change,” and “Sustainability.” Stable system operation is indispensable for attaining such aspirations, and therefore, we continue to position cyber risks such as ransomware damage that may serve as an impediment as top risk of the Company. In order for the management team to lead in responding to such risk, the Company formulated the “Declaration on Cybersecurity Management” (*1) in April 2022. Strengthening of governance, systems, human resources, etc., management of supply chain risk (*2), thorough implementation of cyber hygiene (*3), improvement of cyber resilience (*4), and other such matters have been included as the specific policies for cybersecurity measures, and to realize the foregoing, the Company secured at least 5% (*5) of the budget for IT investment under the Medium-Term Management Plan as cybersecurity-related investment.
In addition, in January 2023, we established the Cyber Defense Center, which oversees cyber risks for the entire Group, in order to strengthen our organization. In the March of the same year, in order to promote cybersecurity mutual aid beyond our group framework, we established "CMS-CSIRT" together with the 6 banks participating in MEJAR and the 13 banks participating in the NTT Data Regional Banks Cooperation Center.
While the Concordia Financial Group has disclosed the progress of its cybersecurity measures in its Integrated Reports and in such other ways, this Report has been created with the aim of and focus on introducing our daily efforts and future directions related to cybersecurity to all stakeholders. We hope this Report helps you in deepening the understanding of our activities.
Toshihiko Onuki
Officer in charge of ICT Management Department (Security officer)
Concordia Financial Group, Ltd.
- (*1)
- (*2)
Risk of cyberattacks that may occur at an outsourcee, etc. outside the Company.
- (*3)
Cyber hygiene refers to countermeasures against cyberattacks which are as basic as hygiene control.
- (*4)
An ability to minimize damage and make swift restoration in the event of a cyberattack.
- (*5)Investment ratio on par with global standards (Research by a foreign research firm).
Cybersecurity Governance
Organization
From FY2023, we have formed a Cyber Security Office within the ICT Management Department and established a Cyber Defense Center within that office. The Cyber Defense Center consists of the CFG-CSIRT (*6), which comprises the CSIRT members from each Group company, and a private SOC.
The CFG-CSIRT promotes cybersecurity governance for group companies and regularly coordinates cybersecurity information with the MEJAR banks, while the private SOC utilizes the latest integrated log monitoring tools and automation tools for early detection and handling of security incidents.
In addition, we have an advisory contract with an outside attorney specializing in cyber security to ensure that the legal aspects of various responses are verified.
- (*6)Abbreviation for Computer Security Incident Response Team. An organization to respond to security incidents
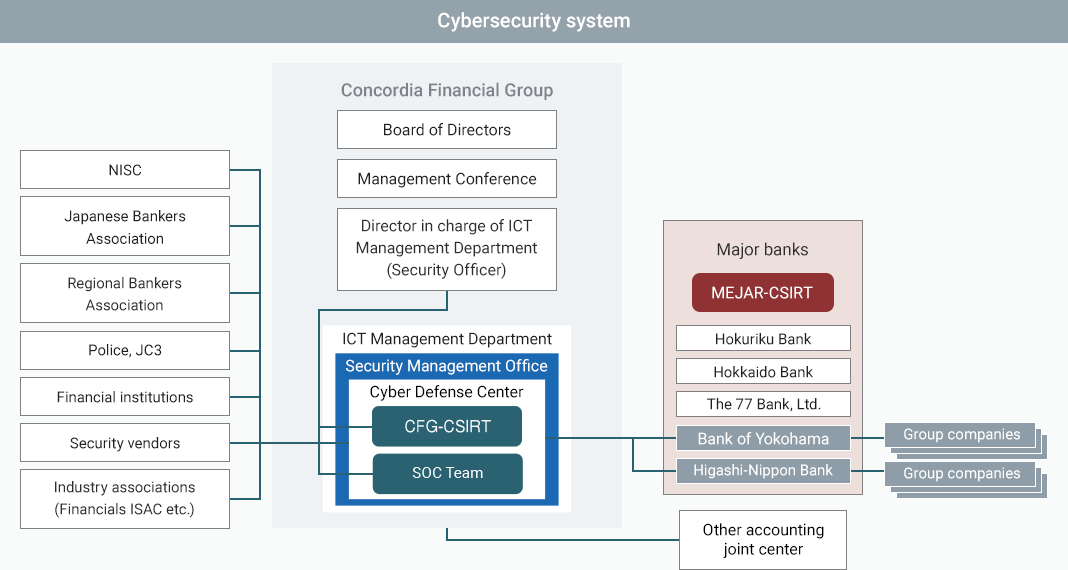
Involvement by the management team
The “Declaration on Cybersecurity Management” was formulated in April 2022, to clearly state that our cybersecurity measures will be led by the management team. In terms of the framework, the officer in charge of the ICT Management Department is defined in our Security Policy as Security Officer who oversees security of the Group as a whole. In addition, a framework has been established in which threats, regulatory developments, security countermeasures based on the foregoing, and the current situations are reported as part of agendas of regular meetings of the ALM and Risk Management Committee mainly consisting of Directors, reports to President, CSIRT meetings, etc. and the management team provides instructions and conducts checks regarding reported matters appropriately.
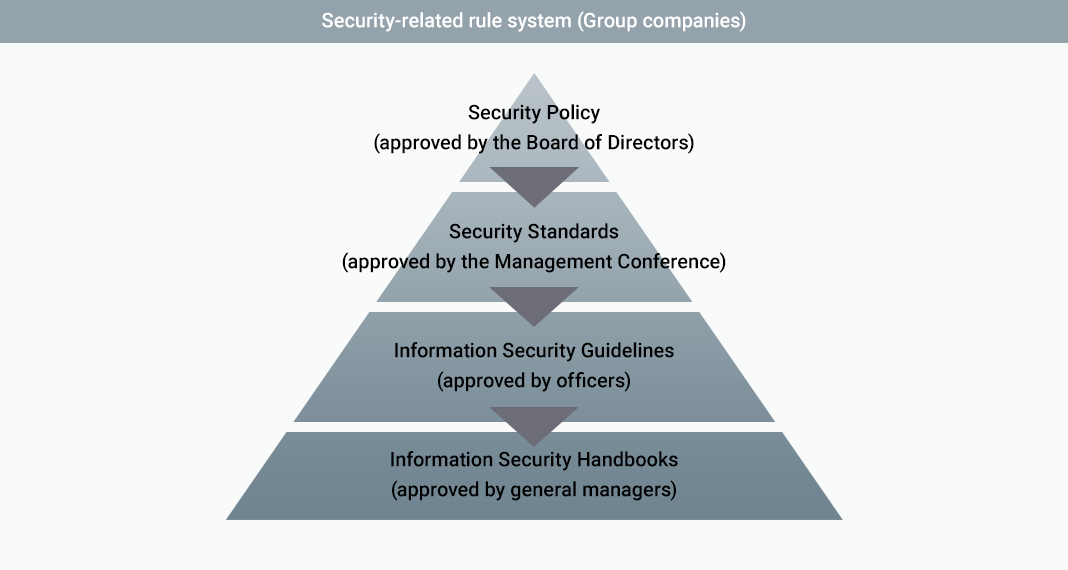
Rule system regarding security
With the Security Policy established by the Board of Directors of the Company placed at the top of the hierarchy, more
detailed provisions including Security Standards and Information Security Guidelines have been established within the
system to ensure consistent and stable conduct of operation and the safety of information assets. In addition, regular
reviews and amendments are carried out to reflect legal reforms and trends.
The Company’s policies have been
penetrated into every corner of Group companies as they are required to establish their own security policy based on the
Company’s Security Policy.
Information management framework
The Group possesses a large amount and various types of information including customer information and management information. In order to manage such information appropriately and thereby prevent leakage of information to external parties and prohibit any persons without business necessity from accessing such information, in addition to implementing physical and information system-based access controls, the Group has put various regulations and rules in place, which strictly establish classifications and definitions of information, and thoroughly implements these regulations and rules among officers and employees. Security reviews on system specifications are conducted by dedicated security system-risk personnel during planning and development phases, and vulnerability diagnoses are carried out by external security vendors before systems go live, as well as on a regular basis after going live, whereby a high level of safety is ensured.
Personal information such as customer information is encrypted using dedicated tools when stored in our systems, and communications are also encrypted when customers access our official websites and Internet banking systems using their devices. The heads of relevant departments, who are also in charge of security of each system, are responsible for management of such information and the Audit Department conducts checks from an objective viewpoint. In such ways, we work to handle customers’ personal information safely and appropriately. In addition, we conduct credit card issuance operations in compliance with the Payment Card Industry Data Security Standard (PCIDSS), which is an international security standard for the credit card industry.
When using cloud services or entrusting information of the Group to outsourcees, we conduct evaluation on their status of compliance with the Group’s security standards, not only when entering into a contract but also on a regular basis after conclusion of a contract. More specifically, we conduct safety evaluation of systems of service providers and outsourcees and evaluation of their readiness for information management, including education of their employees (including their contract workers, and employees of their subcontractors). If a service provider or outsourcee does not meet our standard, we require it to improve or otherwise replace the service provider/outsourcee with another one.
Information level and definition (excerpt)
| Information classification |
Definition |
|---|---|
| Most critical | Information, such as customer information, shareholder information and personnel information within Group companies, that is accessible only by persons with permission based on their functional authority and is expected to have a significant impact on operations of a Group company in such ways as giving rise to an incident related to protection of personal information through a leakage or loss, among other reasons. |
| Critical | Information, such as regulations and notices, a leakage or loss, among others, of which affects only the Group and specific related parties |
| General | Information, such as disclosed information, which is in the public domain |
Cybersecurity Measures
The Group has identified issues and strengthened countermeasures by conducting external audits based on the “Cybersecurity Framework,” international standard guidelines stipulated by the NIST (*7), as well as TLPTs (*8) through which white hat hackers actually intrude into internal systems to evaluate the vulnerability. In addition to annual TLPTs, since FY2021, the Group have conducted external audits using the “Cybersecurity Assessment Tool (CAT)” of the FFIEC (*9), which is widely used by U.S. financial institutions, and promoted strengthening of measures against identified issues on an ongoing basis, with the aim of attaining the security level on par with global financial institutions.
- (*7)National Institute of Standards and Technology
- (*8)Threat-Led Penetration Test
- (*9)Federal Financial Institutions Examination Council
(Part of) cybersecurity measures planned to be implemented under the Medium-Term Management Plan
- Launch of the Cyber Defense Center (private SOC (*10))
- Automation of security monitoring
- Building of real-time security information dashboards for the management team
- Automation of management of IT asset vulnerabilities and risks
- Sophistication and automation of analysis based on the next-generation SIEM (*12) infrastructure
- Conducting external audits (CAT evaluations and TLPTs) on an ongoing basis
- Using threat intelligence (*13) in the respective fields of strategy, operation and tactics
- (*10)Abbreviation for Security Operation Center. The function has previously been entrusted to security firms.
- (*11)A security concept based on the belief in mankind as fundamentally evil, in which nothing would be judged as secure until verified even within an internal environment.
- (*12)Security Information and Event Management
- (*13)Information that can be used for security countermeasures by analyzing the purposes and means of attackers
Education and Awareness Raising
Education
The Group believes that it is essential to improve cybersecurity literacy among all Group officers and employees.
Accordingly, we conduct drills on suspicious e-mails several times a year and e-learning training at least twice a year
using practical themes (*14) for all Group officers and employees. In addition, we provide new hires, newly appointed
managers, managers in administrative positions, managers in supervisory positions, etc. with level-specific training,
and also hold study sessions by external experts for the management team.
For your information, thanks to the regular drills on suspicious e-mails, we maintain the click rate of URLs in e-mails
used in drills as low as 1%.
- (*14)We have entered into a design partnership with Israeli startup company AironWorks to create practical training optimized for the Company.
Full-time employees of the Cyber Defense Center are encouraged to obtain CISSP and Registered Information Security Specialist certification. (All certification training, acquisition, and maintenance costs are covered by the company.)
We also work to improve the knowledge and skills of our full-time employees by providing training for more specialized international certifications such as the Global Information Assurance Certification (GIAC) and the Offensive Security Certified Professional (OSCP) certification, sending them to security conferences, and sending them to the Institute of Information Security (Master's Program). In addition to this, we have set targets for mid-career specialists and will continue to recruit and train them.
Certifications and qualifications held by full-time CSIRT employees
- CISSP (Certified Information Systems Security Professional)
- Registered Information Security Specialist
- GCIH (GIAC Certified Incident Handler)
- OSCP (OffSec Certified Professional)
- CISM (Certified Information Security Manager)
- CISA (Certified Information Systems Auditor)
- CRISC (Certified in Risk and Information Systems Control)
- PMP (Project Management Professional)
Drills
We participate in a large number of drills throughout a year so that we can take swift and smooth actions in the event of an emergency, and thereby work to maintain the skills and further improve procedures to respond to incidents depending on their type (infection with ransomware, DDoS attack, information leakage, etc.).
List of drills we participate in or conduct
- Cross-financial-industry cybersecurity exercise (Delta Wall)
- Joint exercise with Financials ISAC Japan
- Financials ISAC Japan’s CyberQuest
- NISC’s cross-sectoral exercise
- Drills for the management team
- MEJAR-CSIRT exercise
Awareness raising
In response to an increasing number of fraudulent remittances through phishing and other means, we have become a member of the Japan Cybercrime Control Center (JC3) and gather information regarding financial crimes which exploit the Internet. We post information on techniques used in fraudulent remittances, examples of suspicious e-mails and SMS (text messages) misrepresenting the Company’s name, phishing websites that have been set up, and other information that should be provided to customers as alert, if any, on our website, so our customers can be alerted.
Mutual Aid and Contribution to Local Communities Related to Cybersecurity
Mutual aid with industry associations
We have become a member of “Financials ISAC Japan,” an association with which just under 500 companies have membership, with the aim of improving security of domestic financial institutions as a whole. We participate in working groups, actively share information on a daily basis, and work on measures to improve security under the concept of “mutual aid” with other companies. We have also become a member of the Japan Network Security Association (JNSA) since FY2022 and will work on activities related to security with experts who are from industries other than finance.
Mutual assistance among regional financial institutions
Together with the six banks that participate in MEJAR, including Hiroshima Bank, and the 13 banks that participate in the NTT Data Regional Banks Cooperation Center, we established the CMS-CSIRT organization to promote mutual aid for cybersecurity. We are working to build relationships among the security divisions of the participating banks, share information that contributes to enhancing security, hold study sessions to improve the capabilities of security personnel, and conduct joint security response training and exercises. We will also consider future joint procurement of security products and resource sharing in order to strengthen the security posture of regional financial institutions.
Contribution to local communities
We held “Kanagawa Cybersecurity Forum 2022 Spring,” an event originated in the Kanagawa Prefecture to raise awareness of
cybersecurity, with Kanagawa-based companies and associations playing a central role, which aims to support improvement
in knowledge of security among local companies, students and individuals. Through this event, we strive to provide
participants with useful information which encompasses not only the overview of cyber risk but also examples of actual
measures, trends in cybercrimes and technologies used in measures against them, etc.
We also participate in the “Public-Private Joint Project for Cybersecurity Measures of Companies in Kanagawa
Prefecture,” through which we will promote activities centering on cybersecurity dissemination and awareness raising for
small and medium-sized enterprises (SMEs) in collaborative efforts among industries, governments and academia.
