Risk Management
Basic Concepts
We emphasize risk ownership to promote and embed a risk-aware culture, managing risks based on the following basic policies.
- To minimize the negative impact of economic fluctuations, and to provide stable and continuous financial services as a financial group trusted by the community, the Group will conduct appropriate risk management.
- The Company ensures sound management by identifying, assessing, monitoring, and controlling the risks for the entire Group as comprehensively as possible, and strives to secure stable earnings commensurate with the risks through the appropriate allocation of management resources.
- In order to ensure objectivity and account for the interaction between risks, we strive to quantify and manage various risks in an integrated manner.
Risk Management System
Within the Group, each subsidiary has set up a risk control department as well as a risk management department for each type of risk, thereby identifying, evaluating, and managing risks. The Risk Management Department at the holding company comprehensively manages risks for the entire Group, and an officer in charge of risk, who is separate from the General Manager of the Audit Department, regularly reports on the risk status to the President and Representative Director and the Board of Directors. In practice, each subsidiary conducts appropriate risk management based on its risk profile and reports the risk status to the holding company.The holding company then reviews these reports and provides necessary guidance to the subsidiaries.
The Board of Directors ensures sound and effective risk management for the Group, regularly and continually reviewing risk management policies and processes based on factors such as the Group’s strategic goals and changes in the external environment. The Board of Directors and the ALM and Risk Management Meeting (Management Committee) monitor, discuss, decide, and oversee various risks and risks across the Group.
In addition, in order to foster and instill the risk culture embodied, risk management workshops and training are continuously held for officers, including directors.

Risk Appetite Framework
Risk Appetite Framework (RAF) in Practice
As a risk governance framework, the Group has introduced a Risk Appetite Framework (RAF) to monitor and clarify the type and amount of risk taken on during operations, while taking into account the balance of earnings, risk, and our capital buffer. When formulating the medium-term management plan and budget for each financial year, a risk appetite statement (RAS), which defines the types and amounts of risks that management should willingly accept or avoid, is adopted at a Board of Directors’ meeting. In addition, in order to utilize the RAF as a framework that contributes to ROE improvement and effective capital utilization, the Board of Directors is discussing the enhancement of asset allocation based on capital allocation that takes into account the risk-return ratio of each division. We plan to optimize risk-return, using the RAF to constantly monitor risk assets and their relationship to return, which are incorporated in the budget.
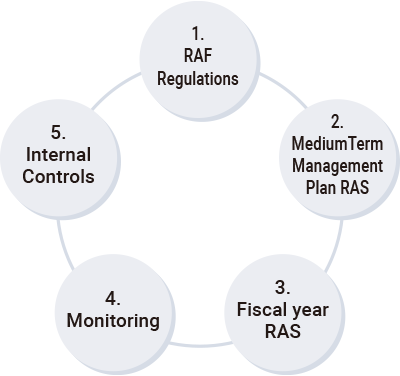
Overview of Risk Appetite Framework (RAF) Management System
A. Capital allocation and risk capacity based capping
The potential maximum loss (risk amount) for each risk is measured using value-at-risk (VaR) and other measures, and capital is allocated to each risk type in order to limit the amount of risk to the amount of equity capital available for risk-taking. For risk assets, the risk appetite is set so as not to exceed measured risk capacity.
B. Stress testing
The Company verifies the appropriateness of risk-taking by estimating losses for each type of risk and measuring the impact on capital, earnings, risk-weighted assets, and risk volume using group-wide stress scenarios to confirm the adequacy of capital in budgetary plans and to ensure that the profit level is acceptable to management in times of stress. In addition, stress tests are conducted based on standards such as the Basel III capital adequacy ratio minimum requirement.
C. Top Risk Management
In order to manage top risks, we set key risk indicators (KRI) as warning indicators in order to as much as possible detect the possibility of risks materializing in the future. We continuously monitor these KRIs to detect early signs of problems and we prepare to respond flexibly in the event that risks do materialize.
The items listed above are monitored, discussed, decided upon, and supervised by the Board of Directors.
Top Management Risks
The Group defines as “Top Risks” those risk events that are important to management and should be managed. We continuously monitor our top management risks and strive to perceive the signs and are prepared to respond flexibly in the event that a risk manifests.
Main Top Risks
- Deterioration in business conditions of companies due to external environmental factors
- Worsening of cash flow due to competition for deposit acquisition and other factors
- Large-scale damage due to cyberattacks
- Major damage due to system failure
- Major natural disasters
- *These are some of the risks that the Company has recognized, but risks other than these may have a particularly significant adverse effect on our business.
Crisis Management
The Group has a crisis management system in place to ensure the safety of its customers and employees, the smooth execution of financial operations, and the protection of customers’ assets even in the event of an earthquake or other large-scale disaster, system failure, infectious disease epidemic, etc. In the event of a crisis, the Crisis Management Committee, which is chaired by the president and representative director, instructs companies within the Group to set up an emergency head office to centrally manage the response to the situation.
Furthermore, we prevent system problems that could have a serious impact on customers and have put in place a problem response system.
The Group places the highest priority on the health and safety of its customers and related parties, and will strive to maintain and continue its financial functions as part of the financial infrastructure essential to the maintenance of social functions.
Integrated Risk Management
Basic Concepts
The Group classifies and manages overall Group risks in the following categories: credit risk, market risk, liquidity risk, operational risk, and reputational risk. In addition, we ensure the soundness of management by identifying, evaluating, monitoring, and controlling risks in an integrated manner to the greatest extent possible, including risks related to the development, provision and revision of products and services, as well as risks related to outsourcing of operations. We are also prepared to secure stable earnings through the appropriate allocation of management resources, commensurate with the risks involved.
- Credit risk
- Risk of loss due to a decline in the value of assets due to deterioration of the financial condition of the borrower
- Market risk
- Risk of loss due to fluctuations in the value of assets and liabilities held resulting from changes in various market risk factors, such as those for interest rates and securities
- Liquidity risk
- Risk of losses due to unexpected outflows of funds (cash flow risk and market liquidity risk)
- Operational risk
- Risk of losses due to inade-quate administration, inadequate systems, violations of laws or regula-tions, natural disasters, and health hazards for executives and employees
- Reputational risk
- Risk of incurring losses due to negative external publicity as a result of the words, actions and behavior of the Group, its officers, employees, etc.
Integrated Risk Management Framework
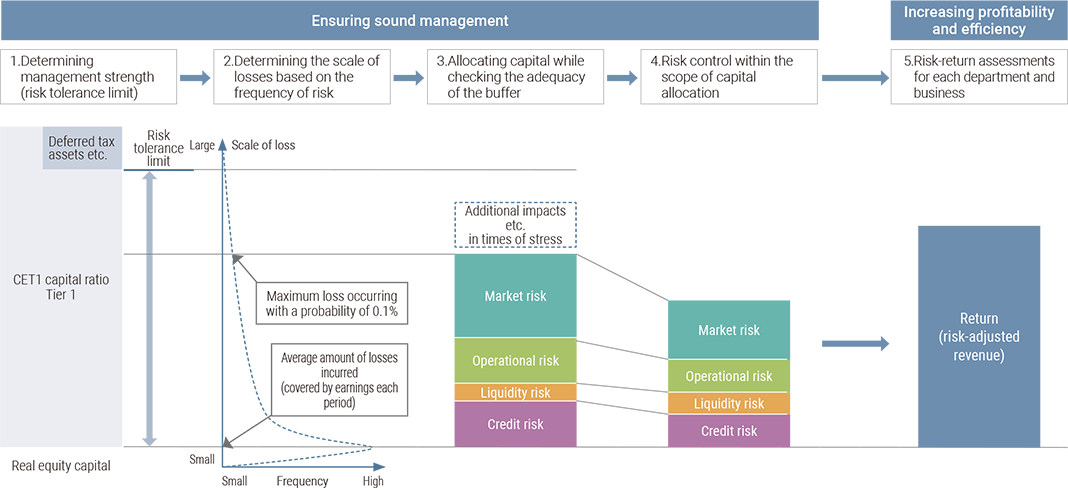
Ensuring soundness through capital allocation
The Group measures the potential maximum loss (amount of risk) for each risk using VaR (value-at-risk) and other measures, and allocates capital by risk type in order to keep the amount of risk within the range of real equity capital (the risk tolerance limit, which is defined as Tier 1 common equity less deferred tax asset equivalents etc.) When allocating capital, we check the sufficiency of the buffer (unallocated capital) to ensure that our real equity capital is not exceeded in times of stress.
Ensuring soundness through stress testing
In order to assess the adequacy of the buffer (unallocated capital) and to confirm the appropriateness of risk-taking, the Group conducts stress tests in which stress scenarios are established and the amount of loss and risk in the event of the stress event is estimated across the risk categories.
Stress scenarios are set for the Group uniformly, factoring in past sharp economic downturns and forecasts of future environmental changes. Stress tests are conducted based on capital adequacy ratio regulations such as Basel III.
Cybersecurity
Cybersecurity Governance
Involvement of Top Management
The Group views cybersecurity as an important management issue and we formulated the “Cybersecurity Management Declaration” in April 2022 to clarify that we implement management-driven cybersecurity measures. In terms of the system, our security policy stipulates that the director in charge of the IT Solutions Department is the security officer in charge of cybersecurity for the entire Group. In addition, at regular ALM and Risk Management Meetings and President Reporting and CSIRT Meetings, which are composed mainly of directors, reports are given on threats and regulatory trends, security measures based on these trends, and their current status as agenda items, and management provides appropriate guidance and checks concerning the contents of the reports. Furthermore, the contents of these reports are reported to the Board of Directors on a regular basis and as circumstances change, and the Board of Directors oversees the execution status.
Third-Party External Evaluation and Internal Evaluation System
In accordance with the “Guidelines on Cyber Security in the Financial Sector" published by the Financial Services Agency (FSA) in October 2024, the Group has undergone an objective evaluation by a third party organization of its governance system, risk management, control environment including outsourcing contractors and its ability to respond to incidents, etc. In addition, we continuously conduct self-assessments specified by FSA to check and analyze the status of our own initiatives. Through this, we strive to improve our ability to respond to changing threats and the effectiveness of our operations from both an objective external perspective and an independent internal review.
Management of Contractors
When using cloud services or entrusting information to contractors, the Group periodically assess whether the contractors and subcontractors comply with our Group’s security standards not only at the time of contract, but also after the contract is concluded. For information of particularly high importance, we verify compliance at least once a year. Specifically, we evaluate the security of the systems of contractors and subcontractors and information management systems including such things as the state of their training of employees (including those of their contractors and subcontractors). When standards are not met, we request improvements or change the subcontractor as necessary.
Protection of Personal Information
As part of initiatives to protect personal information, the Group publishes its purposes of use for personal information in accordance with the relevant laws and regulations. In addition, to prevent leaks and unauthorized access to information, the Group has established rules on access control by granting authorization according to role and rules on the classification and definition of information and ensures that all executives and employees (including part-time and temporary employees) are fully aware of these rules.
At the system planning and development stages, security reviews are conducted by personnel specializing in security and system risk, and security is ensured through regular vulnerability assessments by an external security vendor before and after system installation.When storing personal information such as customer information in our systems, we control access according to role and encrypt the data using dedicated tools. We also encrypt communications when customers connect to our official website and Internet banking from their devices to enhance security. The head of each department is responsible for these systems, for their security, and for managing them. The Internal Audit Department conducts objective checks to ensure the appropriate and safe handling of customers’ personal information. In addition, we run our credit card issuance operations in compliance with PCI DSS, the international security standard for the credit card industry.
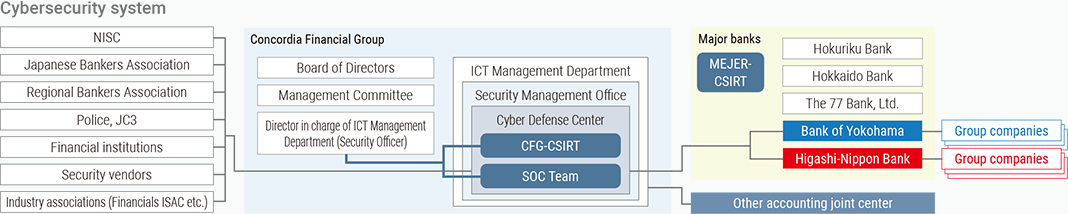
Incident Response System
In order to respond to the evolving threat of cyberattacks, in FY2023 the Group newly established a Cyber Security Office within the IT Solutions Department and established a Cyber Defense Center within that office. The Cyber Defense Center consists of the Group CSIRT, which consists of members from each Group company, and a private SOC.
The Group CSIRT is responsible for collecting and disseminating threat information, as well as investigating and responding to attacks when they are detected. In addition, the Group CSIRT prepares for emergencies by regularly participating in training organized by the National Cybersecurity Office (NCO), the Financial Services Agency (FSA), and Financials ISAC Japan in order to verify cooperation among government agencies, industry organizations, and Group companies. To regularly exchange information, verify systems, and conduct joint training, we have also formed the MEJAR-CSIRT with the regional financial institutions that operate the MEJAR core system and with NTT DATA. Since FY2023, the “CMS-CSIRT” has been established with banks participating in the NTT DATA Regional Bank Joint Center to strengthen the security position of regional financial institutions, through joint training and study sessions, as well as joint procurement of products and resource sharing.
The private SOC utilizes the latest integrated log monitoring tools and automation tools to ensure early detection and quick response to security incidents. In addition to establishing an organizational structure, we have formulated response plans for different types of incidents, such as ransomware infection, DDoS attacks, information leaks. This response plan is continuously improved based on the results of the various drills. In the event of an incident, we investigate the cause and take measures to correct the situation and to prevent recurrence (preventive actions) in cooperation with the relevant departments and strive to respond appropriately.
Education and training
Education and Training for Group Executives and Staff
To improve cybersecurity literacy, the Group provides all officers and employees (including part-time and temporary employees) with training and education based on the Security Policy. To ensure a prompt and smooth response in the event of an incident, drills such as suspicious e-mail drills are conducted multiple times a year. The training is conducted in an e-learning format and covers topics such as recent cyber-attack cases and the protection of information assets. We also provide level-specific training for new employees, newly appointed and existing managers, supervisors, etc. and hold seminars for management-level employees taught by outside experts. Through these efforts, we maintain our cybersecurity skills and continuously improve our response procedures for each type of incident, including ransomware infections, DDoS attacks, and information leaks.
Full-time employees of the Cyber Defense Center are encouraged to obtain CISSP and Registered Information Security Specialist certifications, and they are actively encouraged to participate in external training, seminars and security conferences to improve their knowledge and skills. In addition, we are continuously conducting mid-career recruitment of specialized human resources.
Customer Education
The Group is a member of the Japan Cybercrime Control Center (JC3) and collects and analyzes information on financial crimes using the Internet, in light of the frequent occurrence of fraudulent remittances caused by phishing and other scams.Based on the information we obtain, we promptly identify cases of suspicious e-mails, SMS messages, and the launch of phishing sites, etc., that are using the Group’s name, and take measures to prevent fraudulent remittances by posting a warning on our website and elsewhere.
